So you may or may not be familiar with the popular mobile game DOTS. Well, if you haven’t checked it out, I urge you to. It’s a lot of fun, and it’s available on both Android and iOS.
Anyway, while playing this game, I discovered a stored XSS vulnerability in DOTS. Here’s how it came about.
XSS in a Mobile Game?
So, while playing the multiplayer mode of DOTS, I noticed that there was a “Share” feature. This feature allows you to share (or brag about) your scores with a friend. What happens is that the app uploads your scores and names to the web server (I haven’t looked into the exact HTTP request that it makes), gets back a unique URL, then allows you to send this URL to someone.
After seeing this in action, I decided to see what would happen if I put some HTML tags into the names (<b> tags around my name, and some special characters after Rebecca’s name:
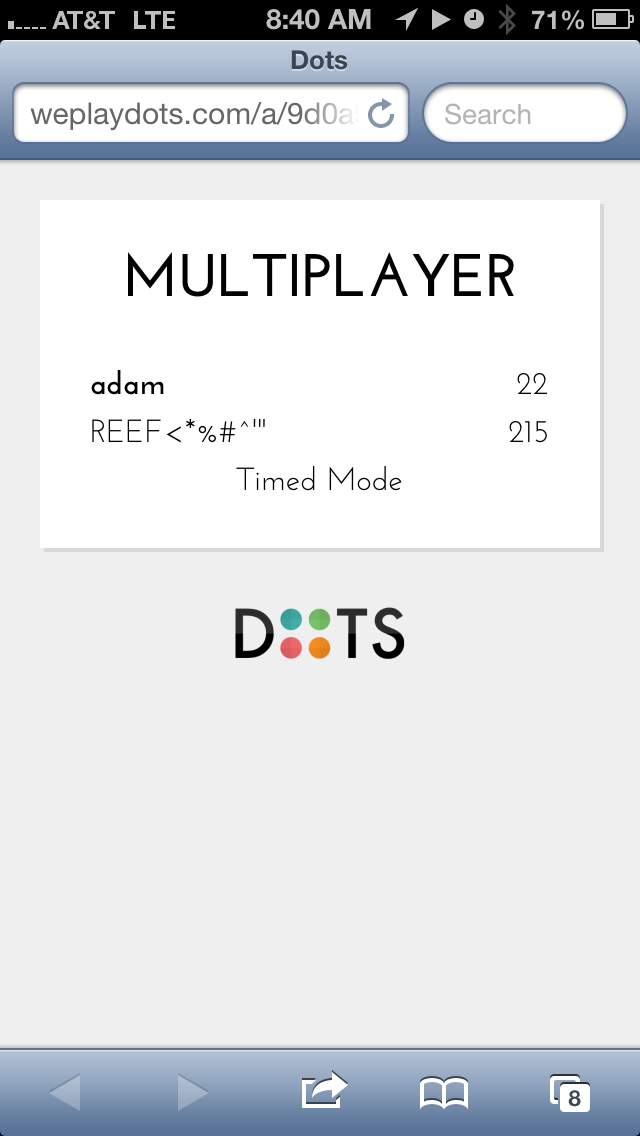
Whoa, my name shows up in bold! I smell an XSS…
Now, what happens if we inject a <script> tag with a call to
alert?
(By the way, it was a lot of fun to do this by typing it into a mobile phone.)
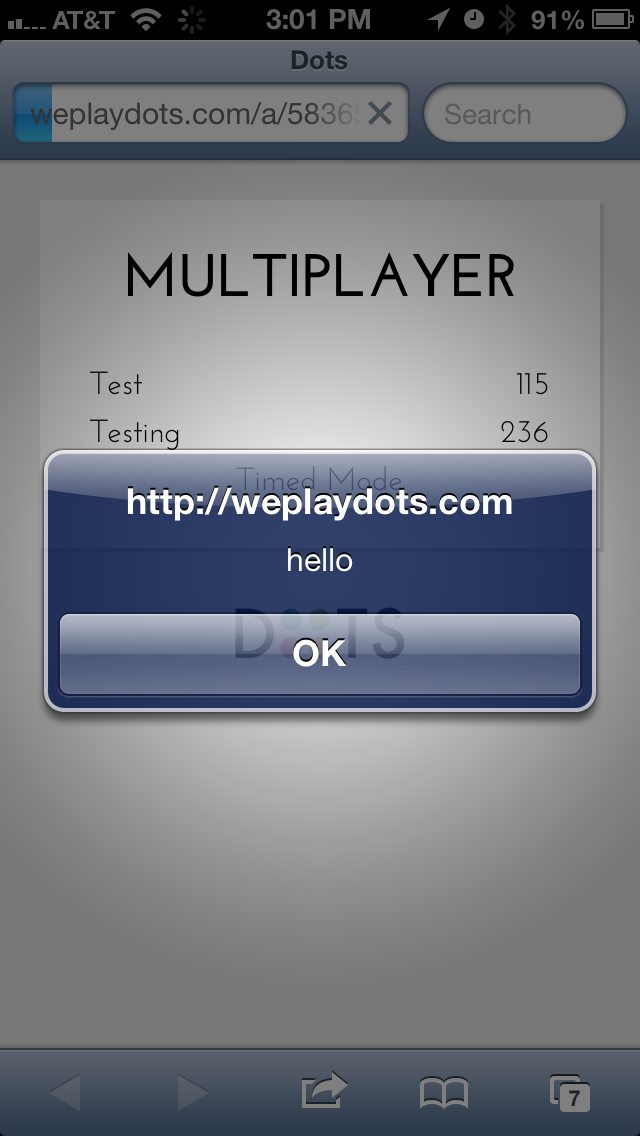
Alright, we’re in business.
Let’s have some fun
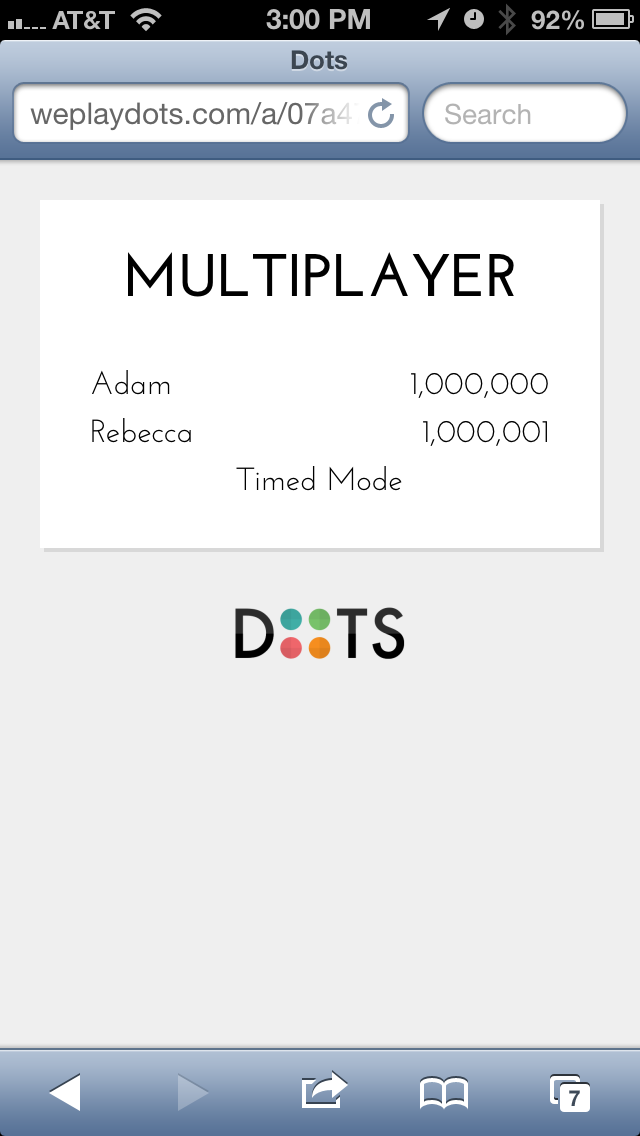
Well, for this game, I thought it would be really interesting to make Rebecca and I have the highest score in the game. I think we succeeded:
Other Bad Stuff
So, what could a bad guy use this vulnerability for?
Infect people who visit the page via a drive-by download. How can you get a lot of people to visit the page? How about the previously described approach of having a crazy high score?
Disclosure Timeline
- 9/1/2013 Vulnerability discovered
- 9/2/2013 Vender Notified
- 9/9/2013 (approximate) Verified Fix
