Assignment 2 (100 points) — Operation Knock-Knock
Assignment 2 is due 2/20/15 at 1:30pm. Late assignments will be decreased at 20% per day (day defined as 24 hour period after the time that the assignment is due).
There is only one part to Assignment 2.
You may work on Assignment 2 either in pairs (two people) or alone. Please email Adam if you plan on working in a pair to let me know the pair.
Description
Your mission, should you choose to accept it, is to write a web application on behalf of the super secret spy agency: CSE591.
You will build a web application that hides in plain sight, with hidden functionality that only our secret agents know exists.
The main functionality of your web application will have user registration, login, logout, as well as, a message board, with users able to post messages.
Each user will have a unique “knock sequence” (described later). Once the secret “knock sequence” of URLs is requested by a logged-in session, your application must switch into “secret” mode. Everything should remain the same, except now secret messages will be shown and posted.
Important: The specification of the URLs must be followed exactly as defined here.
Just as in Assignment 1 Part 3, every HTML page that your web
application outputs must be valid HTML 5. Also, none of your form or
a elements should have an attribute target with the value of
_blank. This is a technique for doing pop-ups and
breaks the automated grading. Plus, it is evil.
URL Interface
Here, all URLs are given relative to the root of your web application.
Assume that your web application is running at
http://example.com:8080, then the URL /user/register described below
would be accessed to the web application at
http://example.com:8080/user/register.
User Management
Users will have usernames and passwords.
/user/register
Required Page Elements:
Form, name attribute of register
Four inputs on the form:
- name attribute of
username, type oftext - name attribute of
password, type ofpassword - name attribute of
password_confirm, type ofpassword - name attribute of
submit, type ofsubmit
Action after submit:
Create a user with the given username and password iff (if and only
if): password matches password_confirm and username does not
already exist.
/user/login
Required Page Elements:
Form, name attribute of login
Three inputs on the form:
- name attribute of
username, type oftext - name attribute of
password, type ofpassword - name attribute of
submit, type ofsubmit
Action after submit:
If the username and password are of a previously registered user, then the user is logged into the system. Once logged in, the knock sequence starts.
/user/logout
No Required Page Elements
When the user accesses the /user/logout page (GET), then the user
will be logged out of the web application. The knock sequence stops.
Message Management
/message/add
Requires logged-in user.
Required Page Elements:
Form, name attribute of create-message
Two inputs on the form:
- name attribute of
title, type oftext - name attribute of
submit, type ofsubmit
One textarea on the form:
- name attribute of
message
Action after submit:
If there is a title and message, then the message is added to the
list of messages. If the user’s session is in “secret” mode, then the
message will be added to the secret messages.
/message/list
Requires logged-in user.
Required Page Elements:
One div with a class attribute of message per message.
Each div must contain the text of the title of the message and the
message content.
Messages by all users are shown. If the user’s session is in “secret” mode, then only secret messages must be displayed (everything else on the page remains the same). If the user’s session is not in “secret” mode, then no secret messages should be displayed.
Knock Sequence Algorithm
Each user will have a different knock sequence, which is a function (in the mathematical sense) of their username.
[
0 : /user/register,
1 : /user/login,
2 : /message/add,
3 : /message/list,
]
Given a username, which is a string, take the md5 hash of the username. Convert it to hexadecimal (there should be 32 hexadecimal digits). The first hexadecimal digit of the hash modulo 4 will be the first element of the knock sequence (using the mapping above), the second hexadecimal digit of the hash modulo 4 will be the second element of the knock sequence, and so on for a knock sequence with total length of 4.
Consider the following example:
For the user who registers with the username “ObMaX” (without quotes), the md5 of this username is “b86ec61e49774117d6ba2b4f183a4a8e” (again, without the quotes). The first four digits of the md5 are [b, 8, 6, e], these digits modulo 4 are [3, 0, 2, 2], so the knock sequence will be [ /message/list, /user/register, /message/add, and /message/add ]
Consider the following example URL accesses (starting as an unknown user):
/message/list
/user/register
/message/add
/message/add
Even though this is a valid knock sequence, the user is not logged in, therefore their application should not be in secret mode. Continuing:
/user/login
Submit form on /user/login with username "ObMaX" and correct password
/message/list
Now, the messages listed are the normal messages. Continuing:
/message/add
Submit form on /message/add with text "Test"
The message with text “Test” just created will be a normal message. Continuing:
/message/list
The message with text “Test” will be shown on this page. Continuing:
/user/register
/message/add
/message/add
The knock sequence has been accessed correctly, and the user is now in “secret” mode. Continuing:
/message/list
The message with text “Test” will not be shown on this page. Continuing:
/message/add
Submit form on /message/add with text "Secret Text"
The message with text “Secret Text” just created will be a secret message. Continuing:
/message/list
This page now contains the message with text “Secret Text”. Continuing:
/user/logout
The user is now no longer in secret mode and is logged out of the web application. Continuing:
/user/login
Submit form on /user/login with username "ObMaX" and correct password
/message/list
There will be a message with text “Test” on this page, and no message with text “Secret Text”.
Knock Sequence Implementation
A knock sequence will only work for a user who is logged in (otherwise how would you know how to calculate the knock sequence).
The knock sequence must be accessed in order, and the knock sequence resets after an out-of-order request among the possible knock sequence requests. Put another way, the knock sequence must be in the exact sequence among requests in the knock sequence.
Conceptually, you can think of the knock sequence as a Finite State Machine (FSM). Consider the following FSM of the previous ObXMaX example:
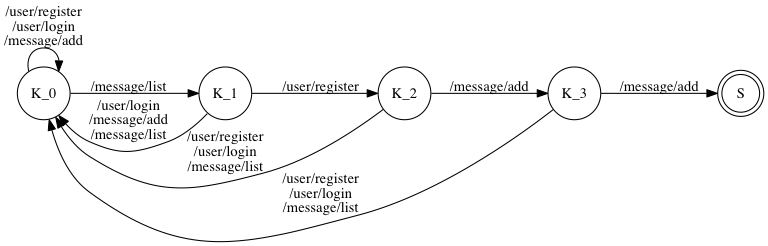
Note that the Finite State Machine does not need to be as simple as the ObXMaX example.
Consider a user with username of “a” (without quotes). The knock sequence for this user is [ /user/register, /user/register, /user/register, /user/login ] and the FSM of this knock sequence is the following:
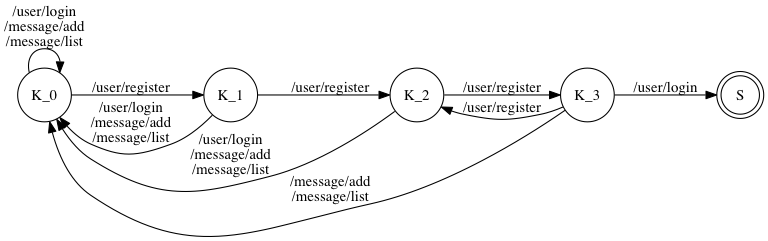
Note that on node K_3, there is a transition from K_3 to K_2
when then input is /user/register. This transition is because the
following sequence is a valid knock sequence:
/user/register
/user/register
/user/register
/user/register (Not secret)
/user/login (Now secret)
This means that you must carefully construct the knock sequence to handle these cases.
Once the knock sequence has been received, the user’s session changes to “secret” mode. Messages added in this mode are secret, and the only messages listed in this mode are secret messages. Secret mode expires when the user logs out.
Implementation
Your program should work on Ubuntu 14.04 64-bit, however this will not be strictly enforced. You can write your program in whatever web programming framework you wish, but you must use a database.
Self Assessment
Please use this self assessment script to test your code before you submit. This will ensure that the automated grading system sees exactly what you see. The first four tests of the automated grading system will be the exact same as the ones in the self assessment.
The file self_assessment.tar.gz is a tar.gz archive of the self assessment scripts.
Requirements
You will need to run the self assessment on a machine with Firefox installed. Also, we are using the python binding for selenium (which communicates and controls Firefox), so you will need to install the selenium pip package (full instructions) like so:
pip install selenium
Running the Self Assessment
Extract
self_assessment.tar.gzusing a command like:tar -xzvf self_assessment.tar.gzChange to the self_assessment directory
cd self_assessmentRun the self assessment
./self_assessment.sh <URL>whereis replaced by the URL of your Assignment 2. This should be the exact same URL that you plan to submit to the automated grading.
The script will run a series of selenium test cases, looking for user forms, user logic, message forms, and user/message logic. Note that this does not check for full compatibility with the assignment description. If the self evaluation script passes with no errors, then you can expect at least 50% on this assignment. The rest of the points will come from fully implementing the application logic.
Submission Instructions
You will need to submit your source code and a README. Your README file should contain your name, ASU ID, and a description of how your program works.
There will be automated grading, along with self assessment scripts.
Along with your source code and README, you will submit a URL where your web application is running. This URL will be used to automatically grade your homework. If you do not have access to a publicly available server, then please use ngrok to create a publicly routable URL to your local machine.
Running ngrok is simple (and multi-platform), run: ./ngrok <port>
and ngrok will give you a publicly routable URL to submit (look at
the Forwarding in the ngrok output. Do not remove or change the
URL until after your assignment has been graded.
Extra Credit (30 points)
Let’s kick the abstraction up a notch. Create a program that takes in a description of a knock sequence web application (the HTML of this page, I want to see some HTML parsing) and generates a web application that implements the description. See, for example this alternative version of Assignment 2
Things that are parameterized:
- Form name attributes
- Form
inputnames - Routes (URLs) of required interface components
- Knock sequence algorithm, specifically the: number of URLs in the knock sequence, order of the knock sequence elements, the URLs themselves (no longer a guarantee that they map to an actual action)
Things that will not change (semantics):
- From
inputtypes - Order of input semantics (in other words, the User Registration form’s inputs will be on the description in the order of username, password, password_confirm, and submit)
- Order of the requred components (first will always be
/user/register - Validation rules
- Action after submit
- Knock sequence hash algorithm